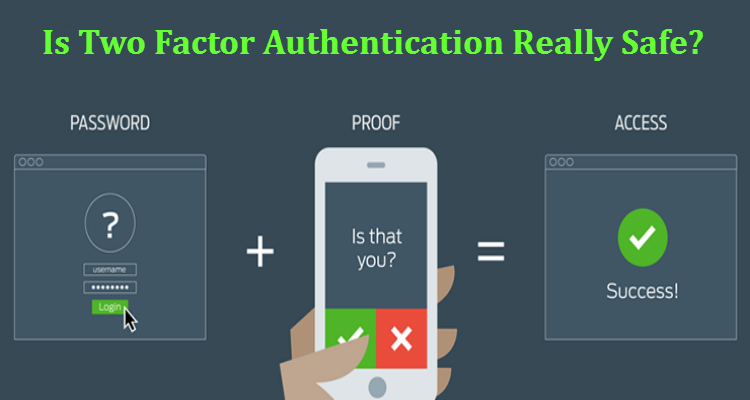
Two-Factor Authentication (2FA) is winding up perpetually prominent as organizations manage developing worries over cyber-insecurity. With 2FA, account-holders approve their personality online by entering a secret key and afterward including a slogan that is created by a comment they have physical access. This "second factor" is not trick evidence, however. DeRay Mckesson, an extremist with Black Lives Matter, had his 2FA-secured Twitter account hacked a year ago. Saving money clients in Germany had their 2FA records captured in May. What's more, in August a bitcoin business person had what might as well be called $150,000 depleted from his virtual wallet. How did a moment factor come up short them? The issue isn't the two-factor authentication innovation. To be more particular, it's not quite recently the two-factor authentication.
It's the full coordination, which incorporates the capacity, accessing, approval, and assertion of character all through the authentication procedure. The criminology on latest hacks uncovers that hackers did not break the verification mechanism itself. Instead, they broke the integration - the identity passing and capacity. The authentication process (single-or two-factor) ought to be evaluated and investigated for weakness. One of the best approach to build security in this method is to evacuate all human connection. You can approve clients in light of big business information or outsider social IDs and other information sources. You would then be able to concede clients reusable two-factor authentication credentials, for instance, a personality card, a portable OATH token, or simply the gadget itself.
Preferably, the registration procedure must be program based, which empowers correspondence to coordinate the customer's local dialect consequently. But each of these functionalities is siloed (e.g., coded after the two-factor item is acquired), and this is the place the hacks happen. The hackers are breaking the frame wall, not the authentication mechanism. Also many times the validation algorithm is hosted or housed on servers or services that are past an undertaking's security control. These servers and services should be examined very carefully because it is very easy for hackers to break the actual identity accumulation form than the real authentication mechanism itself by means of cross-website scripting, SQL infusion, or another assault vector against the frame gatherer.
Numerous validation strategies were made before the resources such as cloud and local mobile applications existed. Therefore common authentication structure, for example, tokens, were intended to utilize dated authentication protocols, like RADIUS, for asset to-information store approval. This kind of confirmation, as a rule, except that there is an intermediary between the asset and the client, which is not generally conceivable in the cloud and with portable applications. Accordingly, endeavors have actualized hackable combination systems that present vulnerabilities in the accreditation accumulation and character passing procedures for these new assets. Cloud assets ought to be secured with cryptographically marked affirmations, as SAML or WS-Fed; comparative systems, including cryptographically approved web administrations, can be utilized for personality going to local versatile applications. Be that as it may, these instruments are just in the same class as the administrations that include the personality passing.
However the authentication system is separate from the character passing framework, your venture needs to guarantee that this exchange procedure is secure every last time. Associations that request impenetrable security must comprehend that genuine security is not in the verification procedure alone. It's just when the whole framework design - from provisioning and approval through declaring character - is tended to form a security viewpoint that individual data will be really sheltered from assault.